XS-Leaks: An Inherent Vulnerability Class in the Web Platform
I’ve written this article for Hackcyom, which is my current company. Please feel free to read the write up on their website: XS-Leaks: An Inherent Vulnerability Class in the Web Platform
This article serves as an introduction to XS-Leaks, breaking down how it works, the common attack techniques and the essential defense strategies.
Note: While XS-Leaks might sound abstract, they have real-world impact. Major platforms like Google, Facebook, and online banking services have all had to adapt their security measures to protect against these attacks.
XS-Leaks (Cross-Site Leaks) are a class of web vulnerabilities that exploit side-channels in the web platform to gather information about users. They leverage the web’s composability and mechanisms that allow different sites to interact, often bypassing the traditional security barriers like the Same-Origin Policy. Unlike other attacks, XS-Leaks do not modify content or perform actions on behalf of users. Instead, they infer information based on subtle side-effects and responses observed during legitimate cross-site interactions.
At their core, XS-Leaks operate by:
- Triggering cross-origin interactions
- Observing side-effects from these interactions
- Inferring sensitive information based on observable differences
XS-Leaks take advantage of small pieces of data exposed during cross-origin interactions. For example, a malicious website could trigger network requests to a bank’s API and deduce if a user has recently purchased certain items based on HTTP status codes. Attackers can infer sensitive information by observing these “oracles,” which typically answer “yes” or “no” to crafted queries.
For instance, by attempting to load a script from bank.com/receipt?q=groceries and monitoring the HTTP status code, attackers can figure out if the user recently bought groceries without directly reading the response. This is a common pattern in XS-Leaks: abusing browser features like error events, frame counts, and navigation behavior to deduce the presence or absence of certain data.
Some common techniques in XS-Leaks include: - XS-Search: A type of timing attack where an attacker brute-forces queries against a search system and infers results based on timing differences. By establishing a baseline for hits and misses, attackers can gradually recover search terms or other sensitive data. - Timing Attacks: By measuring the time it takes for certain actions to complete, attackers can deduce information about the user’s state or data stored on other origins. - Error Events: By triggering errors on cross-origin resources, an attacker can listen for events like onerror to detect if certain resources exist or actions were successful
A more complete list would be: 
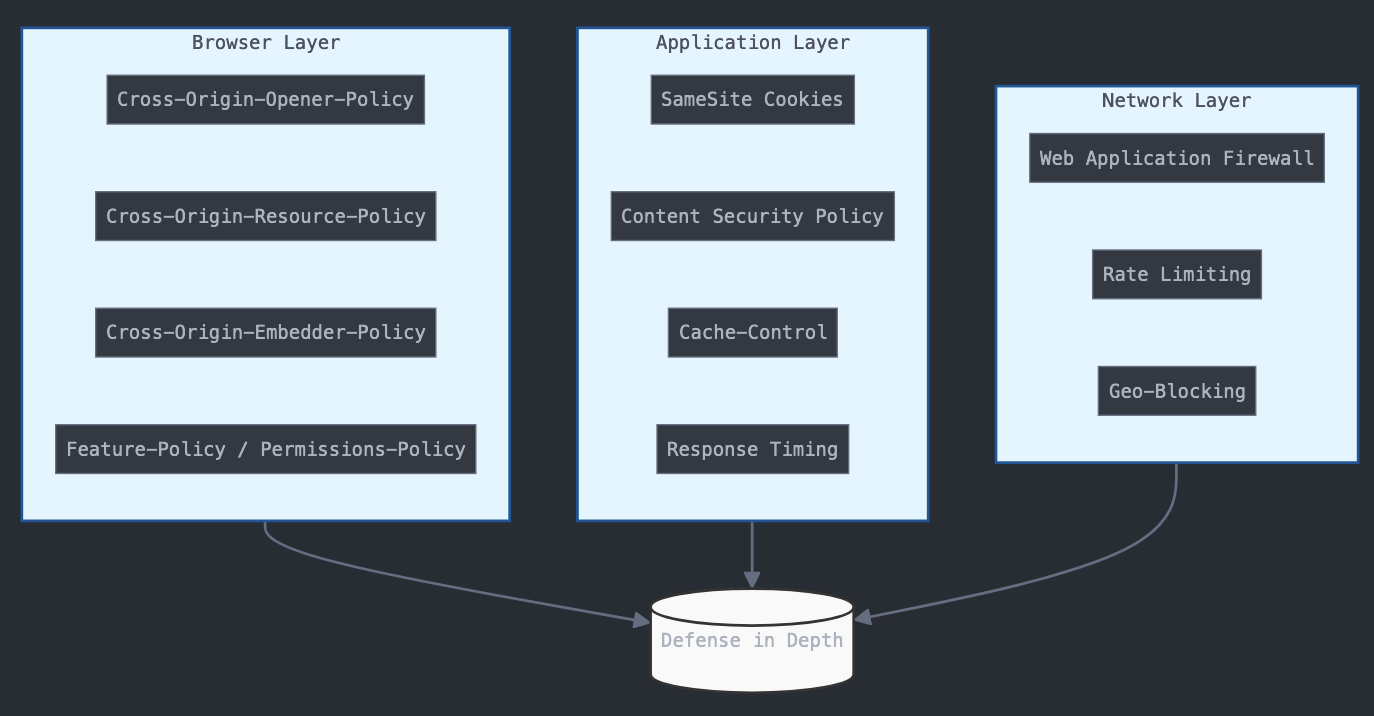
Defending against XS-Leaks
Defending against XS-Leaks is complex due to the inherent nature of the web platform. Effective defenses typically involve a mix of opt-in mechanisms, application design, and secure defaults. Some of the most commonly used defenses include:
1
2
3
- Cross-Origin-Opener-Policy (COOP): Helps prevent attackers from accessing the `window.opener` property, which can be abused to infer user information.
- Cross-Origin-Resource-Policy (CORP): Restricts which sites can load certain resources, helping to contain leaks from cross-origin resource requests.
- SameSite Cookies: By restricting how cookies are sent across sites, applications can limit the effectiveness of many XS-Leaks
Deploying a combination of these techniques is recommended, as no single solution is sufficient to address the wide range of XS-Leak variants. Browser vendors are also working on changing default behaviors to provide more secure defaults, but these changes must balance security and compatibility.
For further details, you can explore the most complete documentation and specific attack write-ups at XS-Leaks Wiki.